Topics
- All Asana features
- You’ve been invited to Asana; now what?
- Navigating Asana
- Different types of tasks
- Set up your ideal workspace
- How to use Asana help resources
- New navigation in Asana
- Asana desktop app
- Create tasks in Asana
- Collaborating in Asana
- Quick-start guide to Asana
- Getting started with Asana’s mobile app
- How Asana works
- Create projects in Asana
- Top features to discover
- Structure your projects clearly
- Assign tasks to teammates
- Comments, messages, and status updates
- Powerful Asana features for work management
- Stay informed with your Asana Inbox
- Maximize productivity with My tasks
- Create projects quickly with templates
- Manage and prioritize your tasks
- Automate and scale your work with the Customize menu
- Find work fast with search
- Connect your tools with Asana
- How to invite team members to Asana
- Reporting with dashboards
- Monitor initiatives and track work with portfolios and dashboards
- Reporting with workload
- Tracking project progress
- Top Asana integrations
- Planning with Asana calendar
- Asana for team leads
- Setting and tracking progress towards goals
- How to choose the right project blueprint for your work
- Plan and execute projects with a deadline
- Customize your projects and portfolios
- Share project updates
- How to cancel your Asana trial
- How to add payment details to a trial
- Make the most of your Asana trial
- My trial has ended, what happens to my tasks, rules, and workflows?
- How to sign up for a free Asana trial
- Purchasing a subscription after a trial
- Set goals during your Asana trial
- Turn your trial into a paid plan
- Invite others during your trial
- Add movement to your workflow
- Multi-home tasks to avoid information silos
- What is a workflow?
- Automate how work moves through stages
- Build the foundation of your workflow
- Assign work automatically with custom fields
- Use dependencies to kick work off at the right time
- Request a task review with a simple automation
- Control how tasks are added to projects
- Building cross-functional workflows in Asana
- Moving your everyday workflows to Asana
- Schedule tasks based on priority
- Form customization
- Task Templates
- Custom fields
- Formula custom fields
- Bundles
- Time tracking in Asana
- Dependency types
- Forms
- Email communication with form submitters
- Filtering and sorting custom fields
- ID custom fields
- Field mapping in forms
- Manual rule triggers
- Rule permissions
- Applying bundles to projects
- Rules integrations for cloud storage and file sharing
- Rule actions
- Sharing a form
- Variables in rules
- Rules integrations for productivity and communication
- Setting dates in rules
- Management dashboard for project templates
- Rules integrations and widgets
- Rule execution history
- Rule triggers
- Rules integrations for operations and support
- Bundles FAQ
- Bundle management and permissions
- Management dashboard for global fields
- Rules integrations for sales and services
- Reference custom fields
- Auto-shifting dates for dependent tasks
- Custom field types and limitations
- How to export all time entry data from Asana as CSV via API
- Conditions and branching in rules
- Approvals
- Workflow builder
- Rules
- Project templates
- Task dependencies
- Microsoft Teams and Asana integration
- Asana for Outlook add-in
- Asana for Gmail add-on
- Zoom meetings in Asana
- Asana for Tableau integration
- Power BI integration
- Google Sheets & Asana
- Google and Asana
- Google Forms and Asana
- GitHub and Asana integration
- Calendars and Asana
- Google Calendar + Asana
- Asana for Adobe Creative Cloud
- Google Smart Chips
- Instagantt + Asana
- Zapier and Asana
- Vimeo and Asana
- Chrome Extension + Asana
- Asana for Jira Cloud FAQ
- Jira Data Center
- Zoom transcripts for automation and AI Studio
- How to create a Zoom call notes workflow with AI Studio
- Enabling permissions for Asana-built and Microsoft 365 integrations
- Outlook Calendar and Asana
- Tray.io + Asana
- ServiceNow & Asana
- Wufoo and Asana
- Web forms & Asana
- Zendesk integration
- Asana for Jira Cloud
- Jira Data Center FAQ
- Asana and Workplace from Meta
- Splunk + Asana
- Salesforce in Asana integration
- Asana in Salesforce AppExchange (being deprecated)
- API
- Asana app in Claude
- Asana app in ChatGPT
- Migrating time tracking data from Everhour to Asana
- Compliance management: API and integration support
- Slack and Asana
- Progress, status, and connecting work to goals
- Goal types and templates
- Goals strategy map
- Write great goals with Asana Goals
- Weighted goals
- Viewing and filtering your goals
- Asana Goals FAQ
- The goal tracking process with Asana Goals
- Lead the goals management process in your organization with Asana Goals
- Goals privacy and sharing
- Get started with Asana Goals
- Email tasks to Asana
- Task actions
- My Tasks
- Scheduling tasks using start dates, due dates, and times
- Text formatting in Asana
- Task fields
- Rules in My tasks
- Converting tasks into projects
- Views in My tasks
- Custom fields in My tasks
- Save time in Asana
- Understanding tasks
- Subtasks
- Task comments and attachments
- Tags
- Custom task types and statuses
- Proofing
- Preparing data for CSV import
- Sections
- Gantt view
- Import data from other tools to projects in Asana
- Understanding projects
- Timeline
- Notes view
- Calendar view
- List view
- Project overview tab
- Managing tasks and dependencies with timeline
- Project owner and members
- Files view
- Critical path on timeline
- Project customization and views
- Gantt view FAQ
- Embedded media project view
- Advanced CSV import options
- Board view
- Shareable notes in Asana
- Project importing and exporting
- Teamless projects
- Project permissions
- Permissions overview
- Read-only links
- Task permissions
- Project privacy settings
- Custom field access levels
- Team sharing
- Forms access permissions
- Edit restriction on custom field values
- Private custom fields
- Asana custom field permissions
- Project admin access level
- Viewer project access level
- Team content permissions for team admins
- Domain-wide admin controls
- Sharing and limiting access to teams
- Team permissions
- Editor access level
- Individual project permissions
- Asana for Agile and Scrum
- Asana for team meetings
- Pipelines
- Ideas and brainstorms
- End-of-month close processes for Finance teams
- Giving feedback and approvals
- How to apply a RACI Matrix in Asana
- Project intake
- Organizational strategic planning
- Resource planning
- Plan and manage company goals
- Using Asana to track customer feedback
- One-on-ones
- Using Asana for project management
- Using Asana for your product roadmap
- Asana for Sales and Account Management teams
- How to use Asana for account tracking
- Video production calendar
- Marketing strategic planning
- Event planning with Asana
- How to create a content calendar in Asana
- Campaign management
- Creative production
- Managing design feedback and critique meetings
- Sharing feedback on AI features
- Asana AI customization
- Asana AI features and admin controls
- Smart goals
- Smart import
- Smart fields
- Smart projects
- Smart editor
- Smart chat
- Create with AI
- Get started with Asana AI
- Smart summaries
- Amazon Q index
- Smart rule creator
- Asana AI FAQ
- Smart status
- AI Teammates
- AI add-on beta services
- Words to workflows in AI Studio
- Work smarter with Asana AI
- AI Studio FAQ
- AI Studio Plus
- Connect your Smart workflow with the right data sources
- AI Studio models
- Writing instructions in AI Studio
- How to structure a prompt in AI Studio
- Create Smart workflows with AI Studio
- AI Studio pre-built AI rules
- How the Use AI variable works
- Troubleshooting in AI Studio
- AI Studio - Human in the loop
- An admin's guide to AI Studio
- Introduction to Asana AI Studio
- AI Studio credit optimization
- AI Studio add-on and pricing
- eDiscovery Resource Center
- Multi-org deployment
- Mandatory two-factor authentication
- Enterprise Key Management (EKM)
- Asana EU Data Centre
- HIPAA Compliance
- Asana and Global Trade Compliance
- How to access the admin console
- Privacy and security
- Two-factor authentication
- Accounts
- Service accounts
- Setting SAML group mapping for licenses
- Multiple accounts and merging
- Data retention policy
- Asana account email policy
- Delete your Asana account
- Managing password settings in the admin console
- SAML group mapping and SCIM interaction
- Access and permissions
- IP allowlisting in Asana
- Compliance management add-on
- FedRAMP Compliance
- Permissions management add-on
- Global authentication settings
- Automatic guest removal
- Mobile apps security permissions
- Understanding user role permissions
- App management and integrations
- Asana Japan Data Center
- SecureAuth for Enterprise Organizations
- Profile field editability controls
- Claiming admin permissions on work items
- Provisioning and deprovisioning users with SCIM
- Asana IP address ranges and hostnames
- Admin security controls
- Admin and super admin roles in Asana
- Role-based access control (RBAC) with custom roles
- How to separate Asana accounts
- Data Residency for Asana
- Setting up Asana roles in Microsoft Entra ID with SCIM
- Authentication and access management options for paid plans
- Setting up Asana roles in Okta with SCIM
- Your Asana account
- Managing an organization
- University organizations
- Managing people in organizations
- Managing teams through the admin console
- Managing organization settings
- A guide to divisions in Asana
- Asana Sandboxes
- Workspaces and organizations FAQ
- Advanced division management
- Division access and management FAQ
- Manage approved workspaces
- Membership and collaboration in workspaces
- Managing members in an organization
- Understanding workspaces
- Managing workspaces
- Introducing Asana Gov
- Managing members and teams in a division
- License assignment in divisions
- Payments in CAD and KRW currency
- Payments in MXN and BRL currency
- Norway VAT
- New Zealand GST
- Indonesia VAT
- Iceland VAT
- EU VAT
- Changes to automatic payments in India due to RBI regulations
- Australia GST
- Adding payment methods for manually invoiced customers
- Upgrading or changing your Asana plan
- United Kingdom VAT
- United States sales tax
- Switzerland VAT
- South Korea VAT
- South Africa VAT
- Singapore GST
- VAT/GST & Sales Tax
- Accessing your billing page
- Payment methods and invoices
- Billing settings in the admin console
- Billing
- Subscription management and upgrades
- Philippines VAT
- Canada GST/HST, QST, and provincial sales tax
- Security and billing for divisions
- How to cancel your Asana plan
- Learn about Asana Premium features
- Learn about Asana Legacy Enterprise features
- Divisions
- Learn about Asana Starter features
- Learn about Asana Advanced features
- Modify your Asana plan
- Manage your growing Asana subscription
- Learn about Asana Business features
- Asana Personal Plan details
- Pricing and purchases
- View only
- Asana for nonprofits
- Asana subscriptions and pricing
- Troubleshooting browser and connectivity issues
- Accidental deletion
- Tasks and subtasks
- Security and permissions
- Navigation and display
- Upcoming discontinuation of personal projects spaces
- Asana Forum basics
- Salesforce AppExchange Integration Deprecation FAQ
- Asana Certification FAQ
- How do I get support from Asana?
- Recover deleted tasks, projects, and more
Provisioning and deprovisioning users with SCIM
Available on Asana Enterprise and Enterprise+ tiers, as well as legacy tier Legacy Enterprise. SCIM is available for organization-wide plans, but not for divisions.
Visit our pricing page for more information.
With SCIM functionality, super admins can quickly and easily provision and deprovision users in Asana from their identity management provider. Your organization can also be used to configure with SCIM. SCIM provisioning allows super admins to:
- Create a new user
- Update a user's profile attributes (Okta and Microsoft Entra ID only)
- Import Asana users into their identity management provider
- Import Asana teams into their identity management provider (Okta only)
- Create teams in Asana from their identity management provider (Okta and Microsoft Entra ID only)
- Deactivate a user
The following provisioning features are not supported by Asana:
- Reactivating users
- Deleting teams in Asana
Note
Like what you see? Get started with a free Asana trial today. Try for free
Set up provisioning
To use SCIM provisioning, you will need to connect your organization's Asana account with one of our supported identity providers. Setup will vary according to the identity provider you use. Asana supports SCIM provisioning via:
- Microsoft Entra ID - Visit the Asana - Microsoft Entra ID integration tutorial
- Google Workspace
- Okta
- OneLogin
Okta
Features
Super admins can easily provision and deprovision users in Asana from Okta. The integration between Asana and Okta relies on an industry-standard protocol called SCIM that allows super admins to:
- Create users: Okta users assigned to the Asana application in Okta are automatically added as members to your organization in Asana.
- Update user’s profile attributes: Attributes such as userName, title and department for a user’s profile can be synced from the user’s Okta profile to Asana.
- Import users: Users created in Asana can be imported in Okta either matched against existing Okta users or created as new Okta users.
- Import groups: Teams created in Asana can be imported as groups in Okta. Take into account Okta doesn't allow you to manage memberships of these imported groups.
- Push groups: Groups and their members in Okta can be pushed to Asana (as Asana teams and team members).
- Link groups: Existing teams in Asana can be linked to groups in Okta after importing the teams from Asana.
- Deactivate users: Users can be deactivated in Asana if they are no longer assigned to the app in Okta.
The following provisioning features are not supported at the moment:
- Reactivating users
- Deleting teams in Asana
Note
Importing users or groups with emojis in their names to Okta will cause failure, as Okta only supports characters encoded with 3 bytes or fewer.
Requirements
Please ensure that you meet the following requirements before turning on SCIM for your organization.
- You’re a super admin for an organization in Asana that’s on the Enterprise, Enterprise+, or Legacy Enterprise tier. SCIM is available for organization-wide plans, but not for divisions.
- You have the correct Okta plan for provisioning users via SCIM. Please see Okta’s lifecycle management offerings for more information.
If you meet these requirements, use the following steps to enable SCIM for your organization.
Steps
Step 1: Add Asana’s Okta integration app to your Okta account
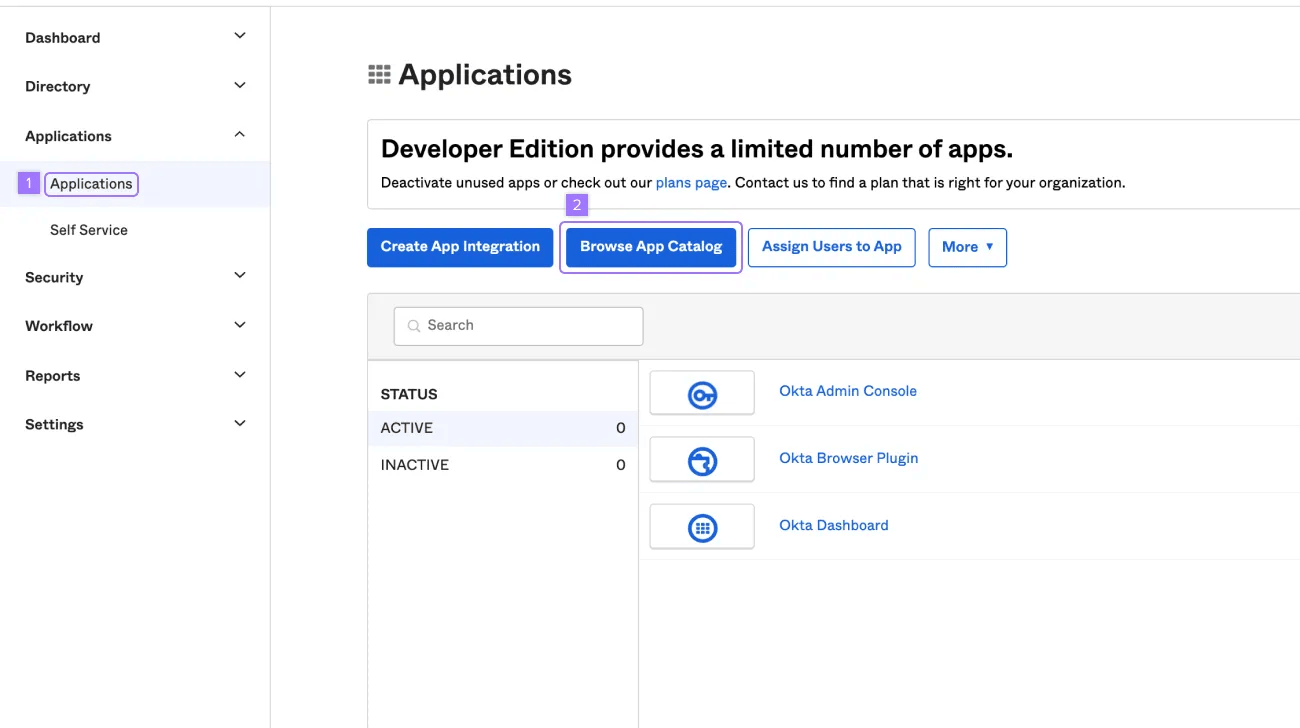
- Click Applications on the sidebar
- Click Browse App Catalog
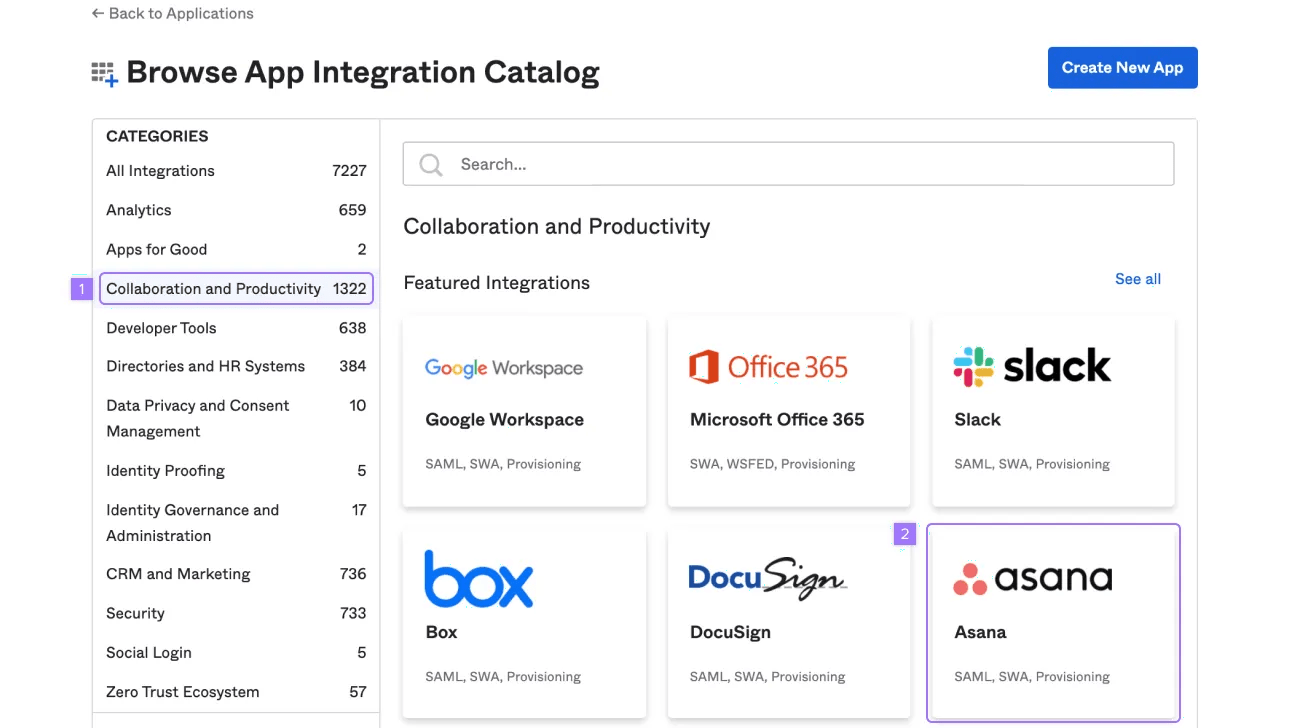
- Click Collaboration and Productivity
- Click Asana
Step 2: Connect your organization’s Asana account to your Okta account
To use SCIM provisioning, you'll need to connect your organization’s Asana account with your Okta account.
Complete the following steps in Asana
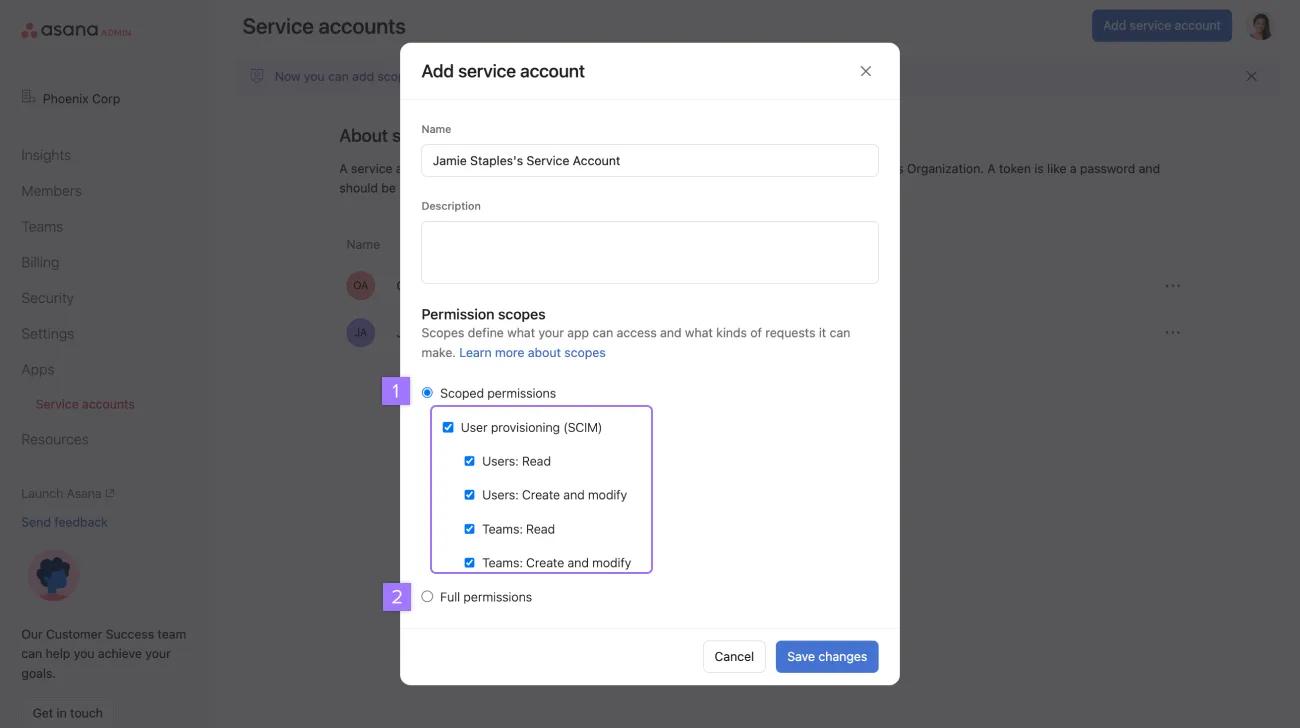
Login to a super admin account on Asana, and navigate to the admin console menu by clicking on your profile picture in the top right, and clicking Admin console. Navigate to the Apps tab and click Add service account.
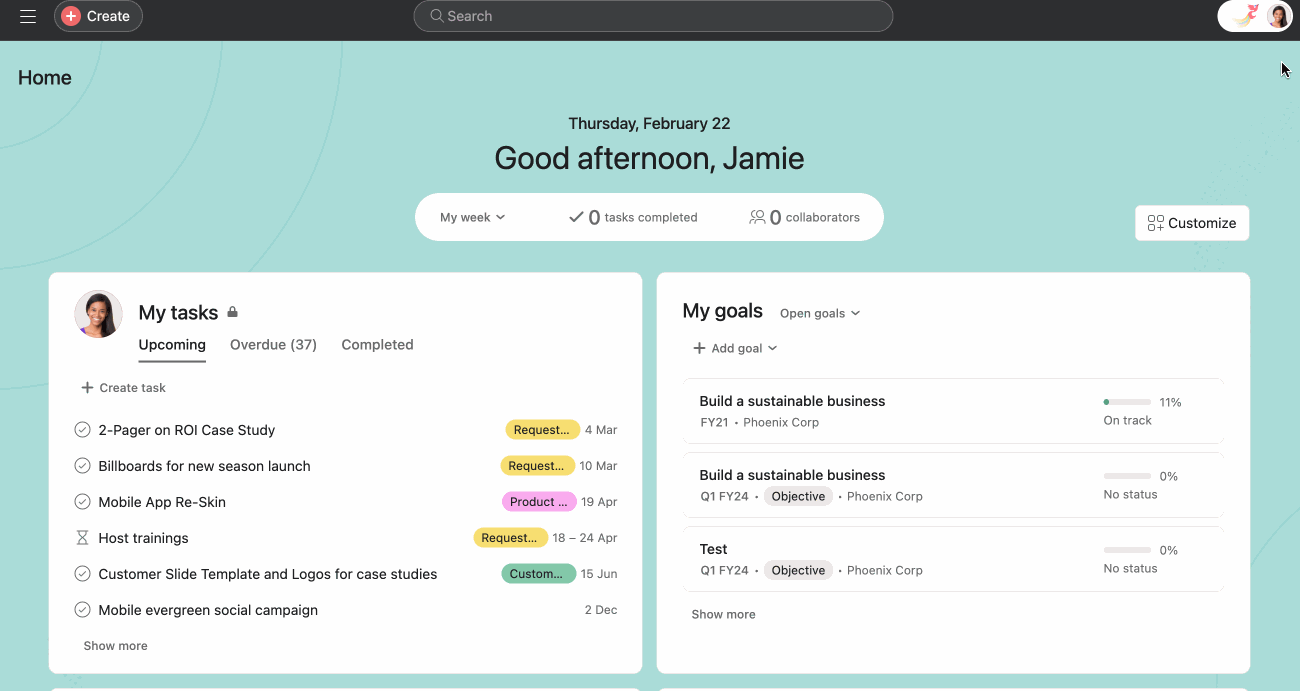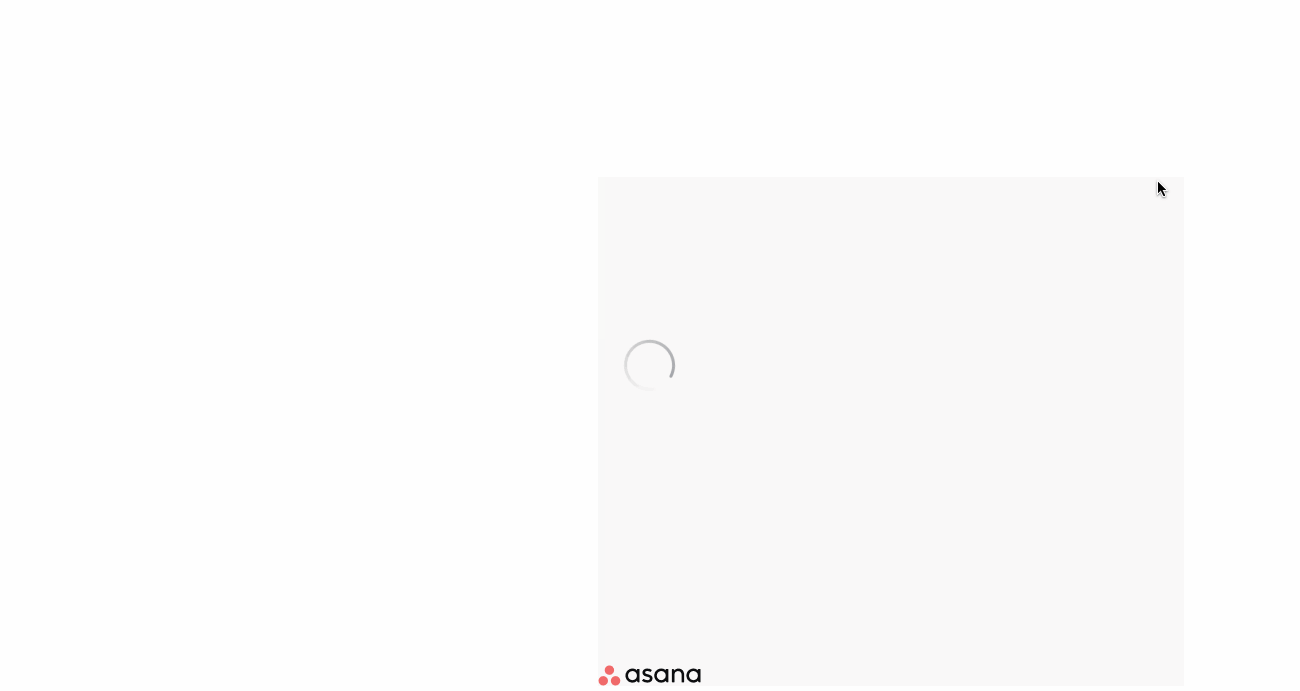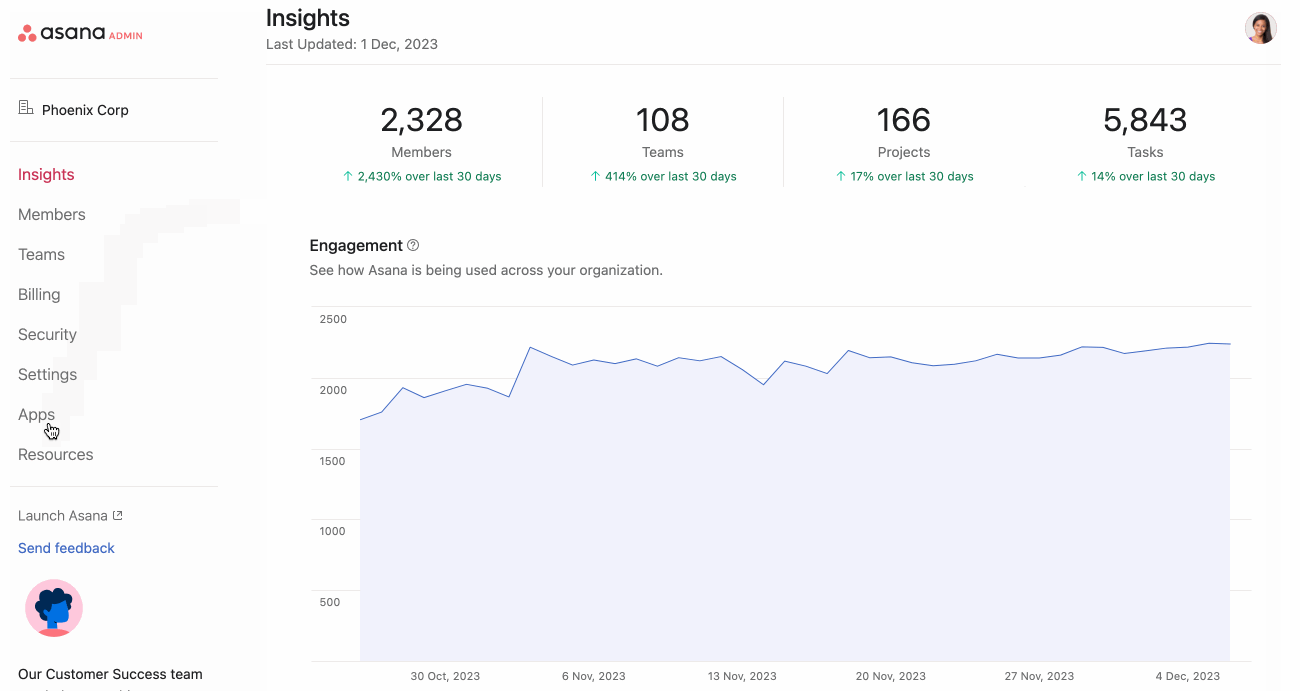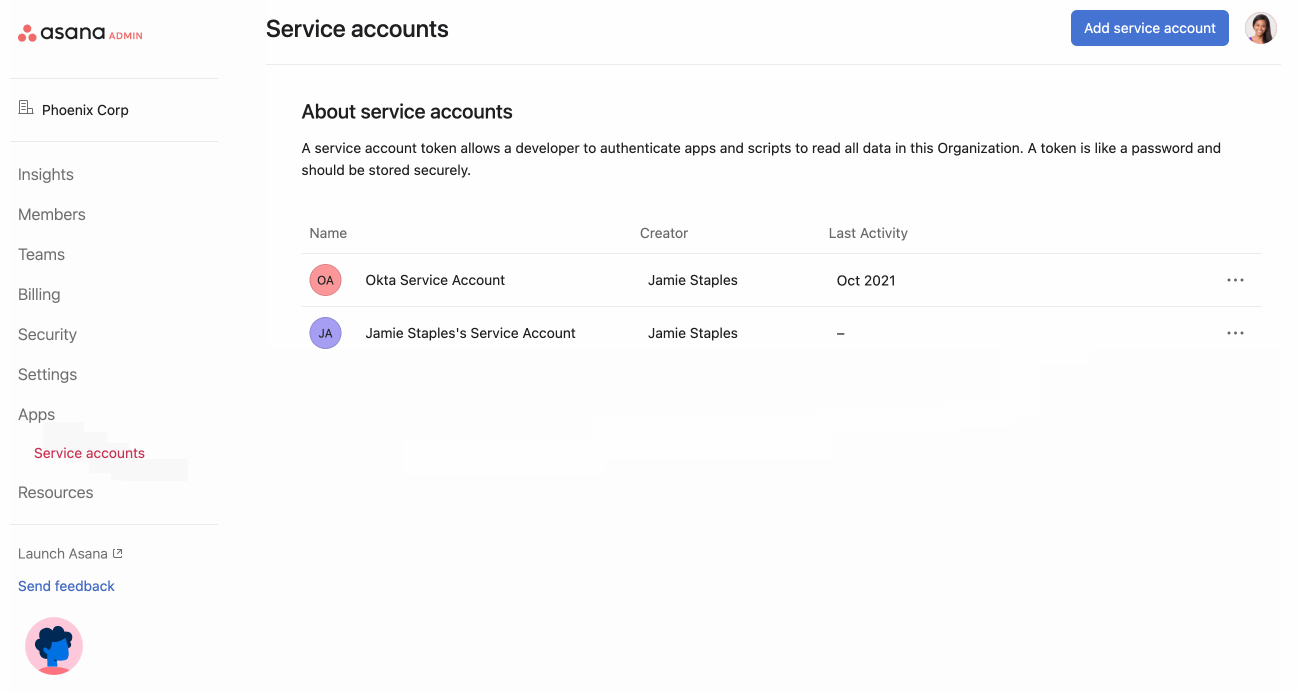
Note
If you don’t want Okta to push groups to Asana teams, rename teams, or modify teams, then uncheck the team-related permissions.
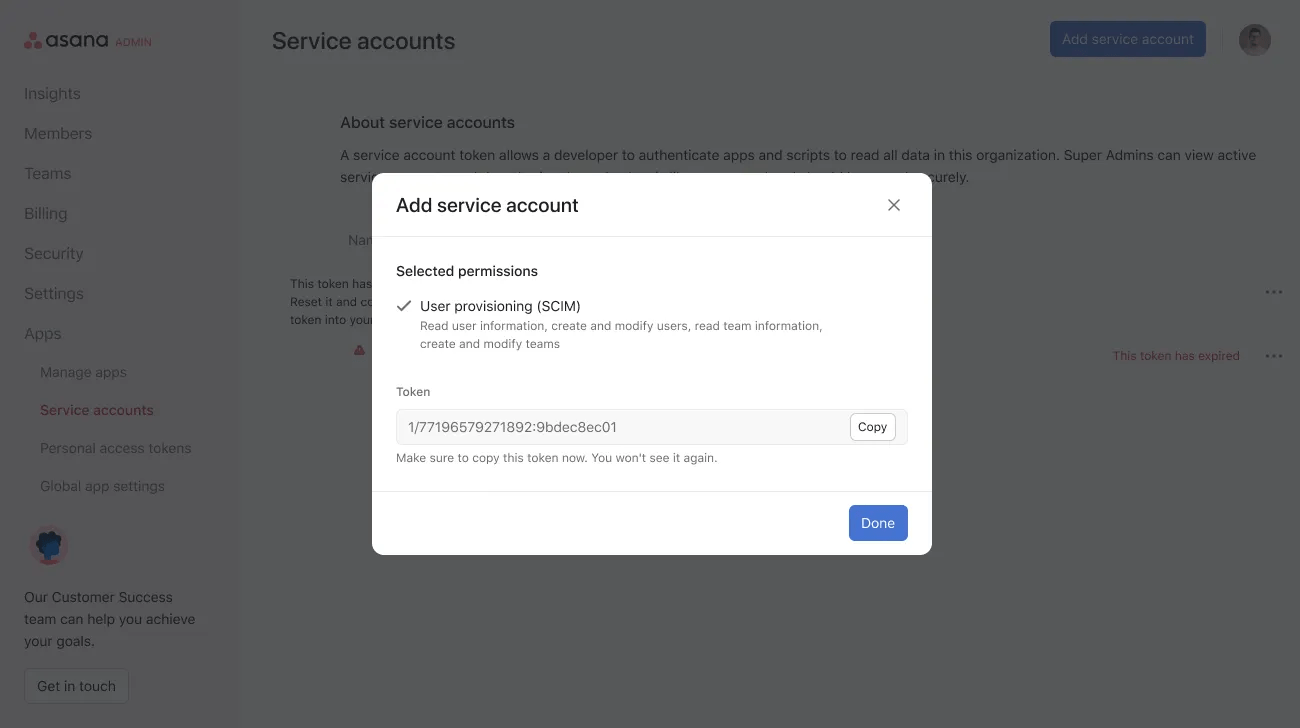
Complete the following steps in Okta
Login to your Okta admin portal and under the Applications tab, navigate to the Asana application.
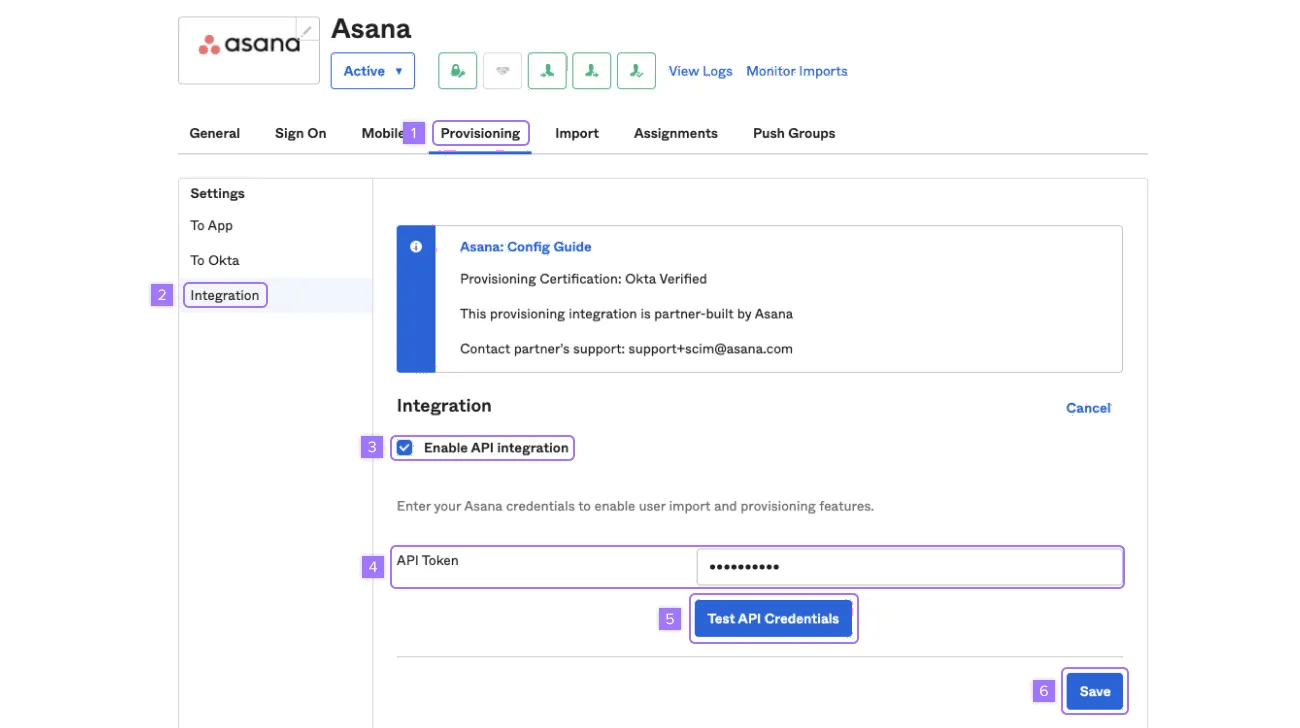
To connect Asana to your Okta account:
- Click on Provisioning
- Under the Settings sidebar click on Integration and click on Configure API Integration
- Check the Enable API integration box
- In the API Token field, enter the token you received in your service accounts tab in Asana.
- Click on Test API Credentials to verify the token is set up correctly
- Click Save to save your configuration in Okta
Step 3: Set up provisioning options for Asana in your Okta account
In Okta
Under the applications tab, navigate to the Asana app and click on Provisioning.
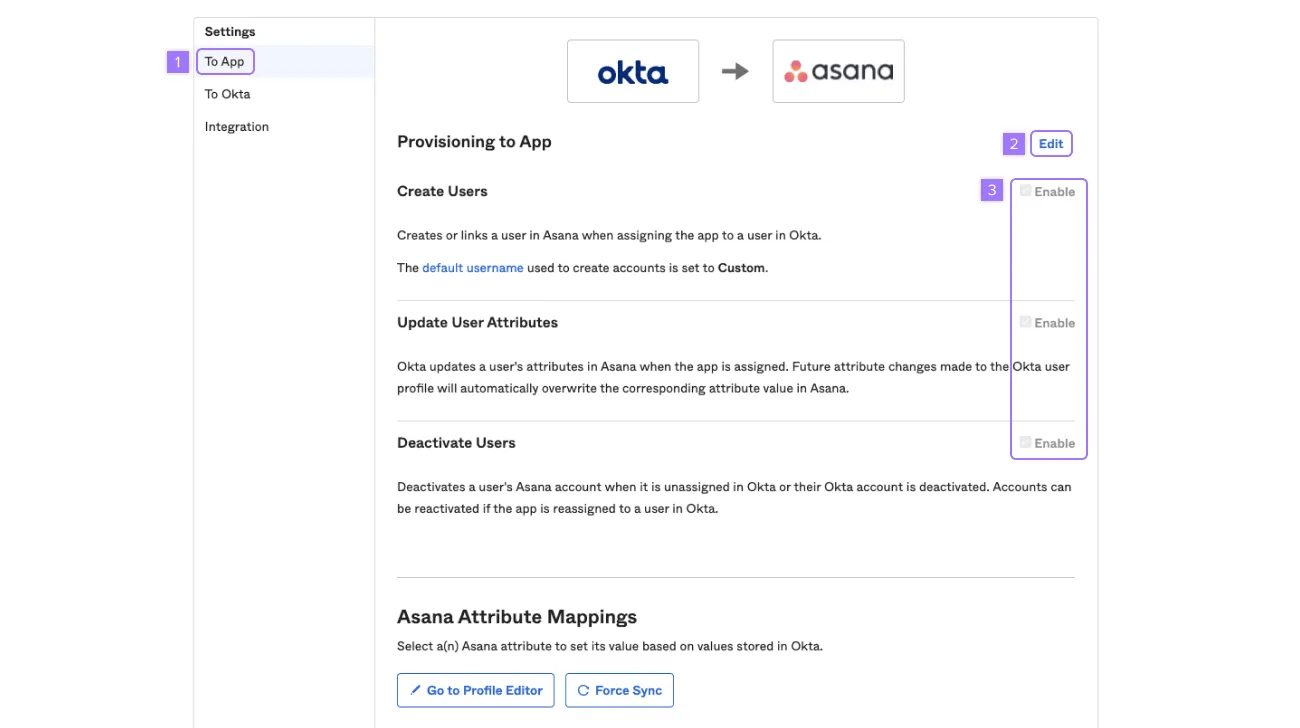
- Under the Settings sidebar click on To App
- Click on Edit at the top right
- Enable user provisioning options for the Asana app and click Save to apply integration settings
Note
We recommend you enable Create Users, Update User Attributes, and Deactivate Users.
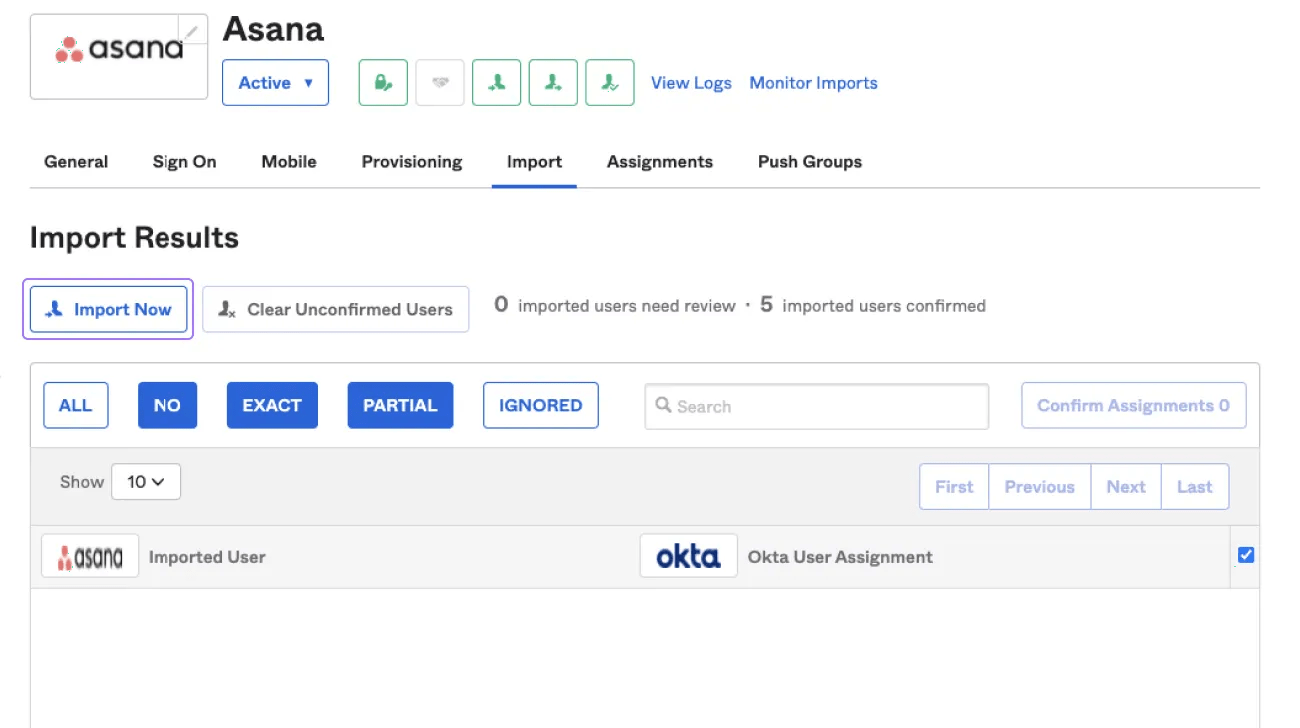
Use the Import tab to reconcile the users detected in Asana with the users you have in your Okta domain. Import any Asana users that you’d like to create or assign Okta accounts for.
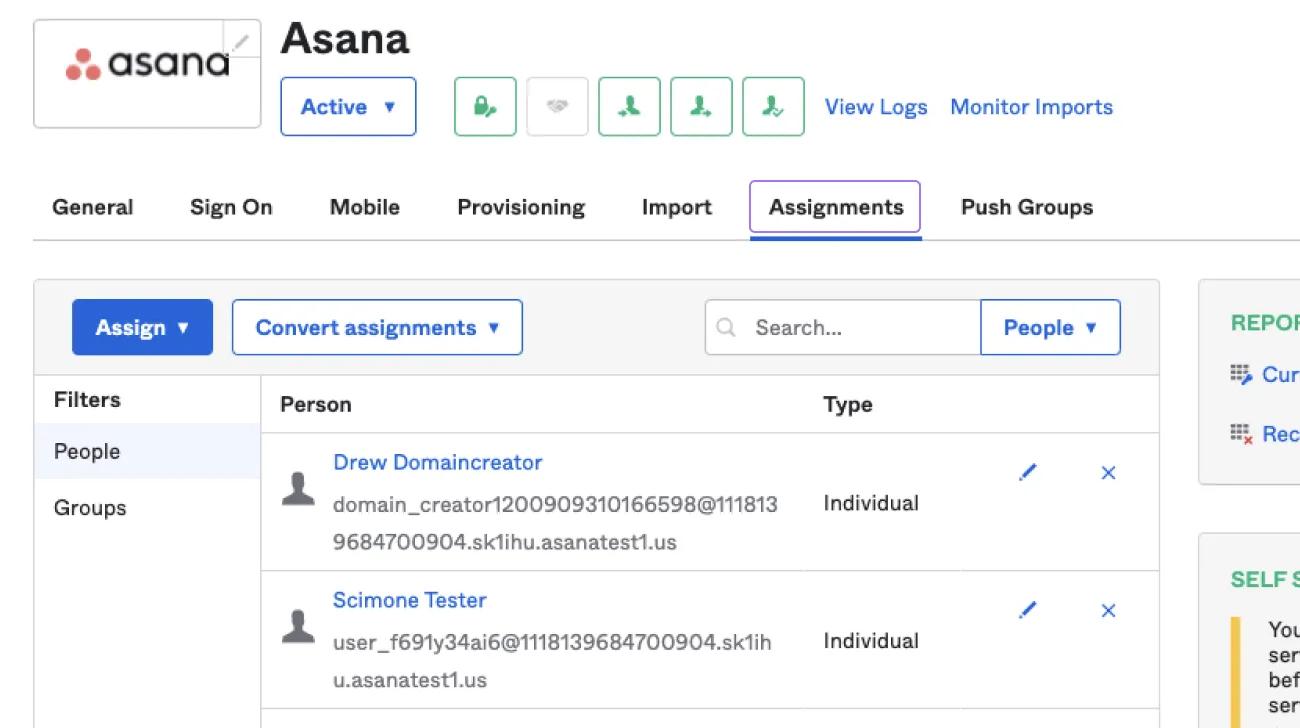
Administer the users assigned to Asana as you would with SAML using the Assignments tab. Users will now be automatically kept in sync with the Asana members list.
Step 4: Map provisioned users into teams in Asana
To map Okta groups to Asana teams, you can decide to push new groups into Asana or link groups in Okta to existing teams in Asana. If you’re linking groups, please ensure that the teams you’d like to map them to are already set up inside Asana. Find out more about how to create a team in Asana.
In the Okta admin portal:
- Go to the Asana app and click on Refresh App Groups in the Push Groups tab to update any imports or changes that occurred in Asana. This ensures that all groups from the target app are represented in Okta.
- Click the Action button (Group Push Settings) if you want the ability to rename a group in Asana when linking. We recommend not renaming the app group to avoid any unintended changes to team names in Asana.
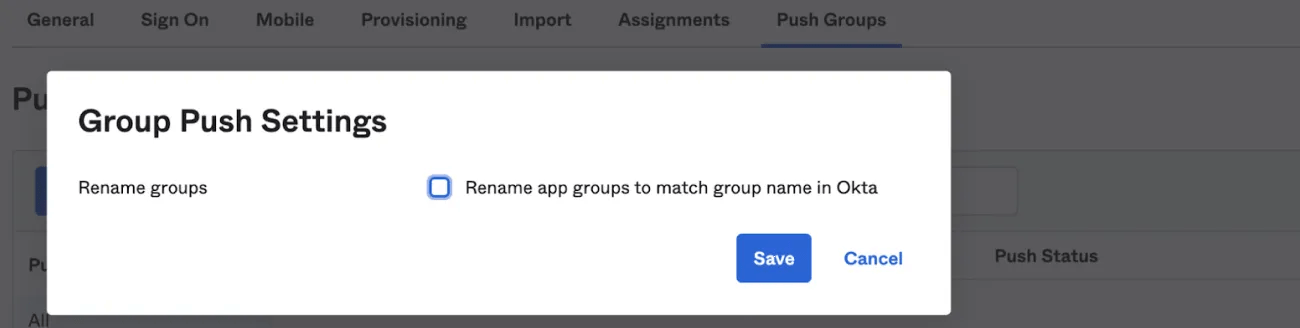
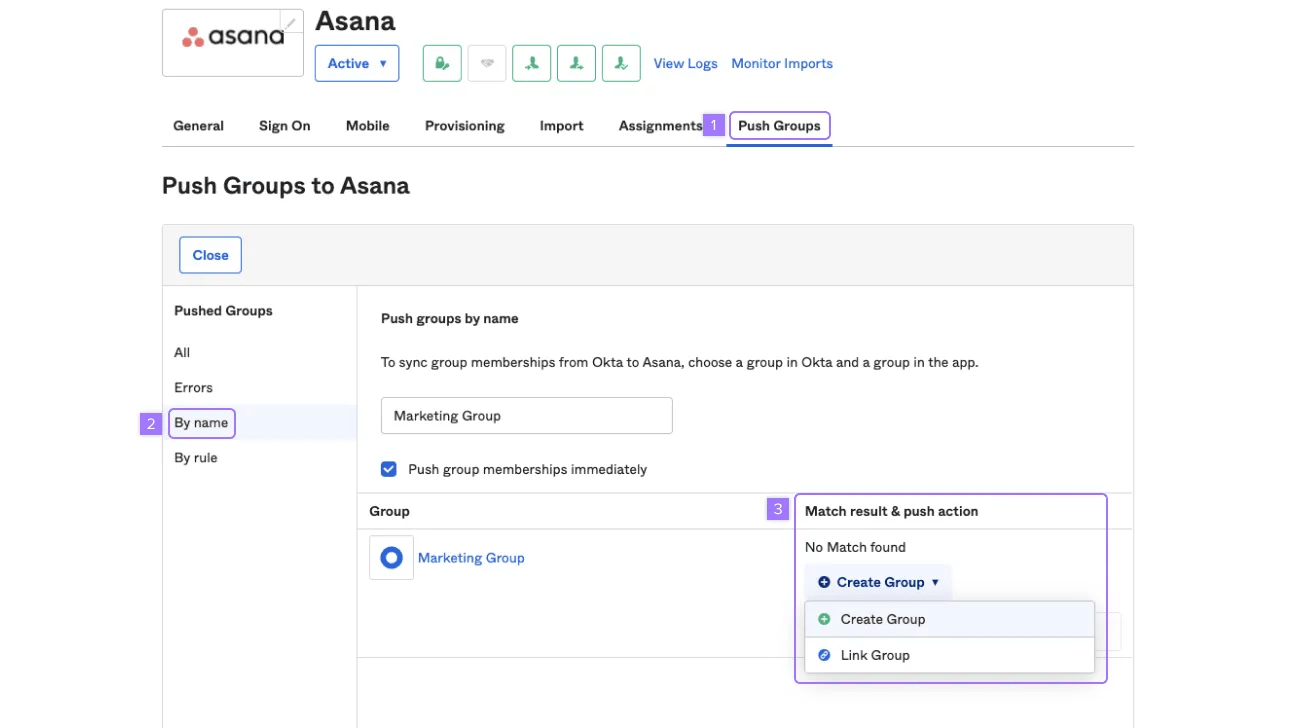
- Click on Push Groups
- Select By name and use a keyword to find the group in Okta
- When the group appears in the table, click the Match results and push action drop-down menu. Choose Link Group if you’re trying to map a group to an existing team. Otherwise, select Create group. Click Save to apply integration settings.
Note
Please note that deletion of teams in Asana from Okta isn’t supported by this integration. Please use the Teams tab in the admin console in Asana to manage and delete teams.
Step 5: Configure attribute mappings for Asana
To configure and map attributes to user profiles in Asana, please follow the following steps.
- Go to the Asana app and click on the Provisioning tab.
- Configure the right options under the Asana Attribute Mappings section.
- Select Create or Create and Update from the choices under the Apply on column.
| Attribute | Type | Info | Notes on limitations |
|---|---|---|---|
| userName | string | Unique identifier for the User, typically used by the user to directly authenticate to the service provider. Each User MUST include a non - empty userName value, and it must be an email address. REQUIRED. | |
| name | complex | The user’s name | |
| name.given | string | Unsupported, use formatted | |
| name.familyName | string | Unsupported, use formatted | |
| name.formatted | string | The full name of the user | |
| emails | complex | Email addresses for the user | |
| emails.value | string | Email address for the user | |
| email.primary | string | Whether this email address is the preferred email address for this user. True may only appear once for this attribute. | |
| title | string | The user's title, such as "Vice President". | |
| department | string | Identifies the name of the department that the user belongs to. | |
| preferredLanguage | string | Indicates the User's preferred written or spoken language. Used for selecting a localized user interface; e.g., 'en_US' specifies the language English and country US. | “Preferred language” can only be set for a user when the user is being created in Asana. Updates to the preferredLanguage field in Okta for existing Asana users don’t get reflected inside Asana. |
| active | boolean | Indicate whether the user’s account is active in Asana. | |
|
addresses |
Multi-valued complex |
The user’s work address | |
|
address.country | string | The user’s country as a two-letter code e.g., “US” | |
|
address.region | string | The user’s region e.g., “CA” | |
|
address.locality | string |
The user’s city e.g., “San Jose” | |
| phoneNumbers | Multi-valued complex |
The user’s phone | |
| phoneNumber.value | string |
The user’s phone number e.g., “543-111-1111” | |
|
User | complex |
Enterprise user schema extension attribute for the user | |
| User.department | string |
Name of the department that | |
| User.costCenter | string |
Name of the cost center the | |
| User.organization | string |
Name of the organization the | |
| User.division | string |
Name of the division the user | |
| User.employeeNumber | string |
A string identifier, typically numeric or alphanumeric, assigned to a person | |
| User.manager | complex |
The user’s manager | |
| User.manager.value | string |
The user ID for the user’s manager |
Step 6: How to update your current Asana - Okta integration
If you’re currently using the Asana - Okta integration, please use the following steps to enable/access the latest updates.
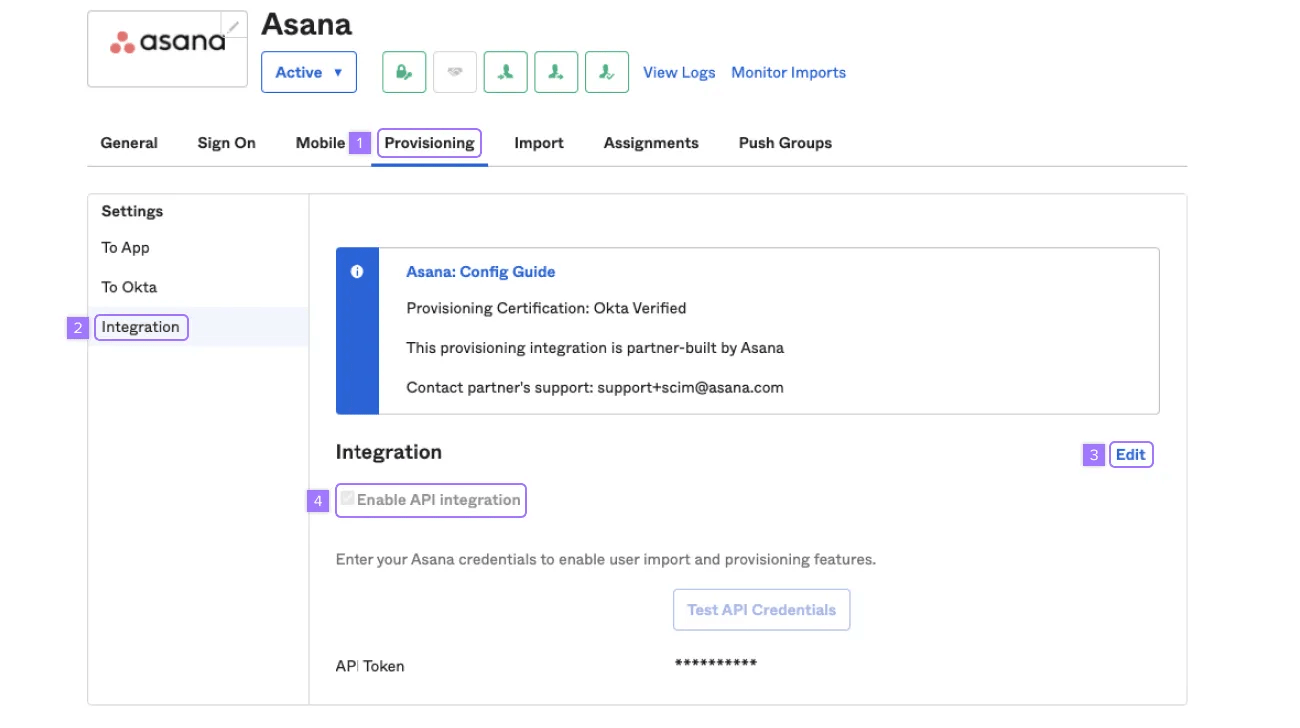
- Click Provisioning
- Click Integration
- Click Edit
- Uncheck the Enable API integration and click Save
Then, click Edit again, check Enable API integration, enter the API token and click Save. Then, enable provisioning features. After this, you’ll see new attribute updates and integration capabilities reflected in the integration.
- When deprovisioning a user from Asana within Okta, the user will be deleted within Asana (same behavior as if the account were removed within the Asana UI). Please exercise caution when deactivating users.
- Assigning the Asana app to users in Okta will create that user profile within Asana, and trigger the same behavior as if they had been invited to Asana. It's important to note this when informing users that they have been assigned the Asana app.
- Changing the Okta username at the Asana application level (i.e. username override) will trigger a deactivate call on the previous username to be issued against Asana. If this previous username was associated with an active Asana account, it will be deleted. Please exercise caution when applying application level overrides.
- When creating or updating users, the users must have emails which match the domain of the organization in Asana (e.g. you can only provision users with an @asana.com email domain to the asana.com Asana organization). Organization guests will continue to be provisioned and deprovisioned, and managed within the admin console's Members tab only.
- A user’s formattedName must match givenName and familyName. When mismatch is found, formattedName takes precedence and could revert/override the givenName and familyName field value changes. So during attribute mapping or manual app user profile updates, please ensure that the formatted name’s value matches the string combination of givenName and familyName during profile push. For example:
- givenName = new firstname
- familyName = new lastname
- formattedName = new firstname new lastname
OneLogin
Learn how to configure SCIM provisioning using OneLogin here.
Note
To enable SCIM functionality with non-natively integrated IdPs please check the necessary accepted attributes here.
SCIM deprovisioning customization
The super admin of an organization can choose how a user’s tasks are handled after they have been deprovisioned via SCIM or the API.
When a user is deprovisioned from Asana, a Previously assigned tasks project containing all of the public tasks that were assigned to the user is created.
An organization-wide setting in the admin console allows you to choose a super admin to become the owner of this project. The project owner can reassign the tasks as they see fit.
To assign the project owner role to a super admin:
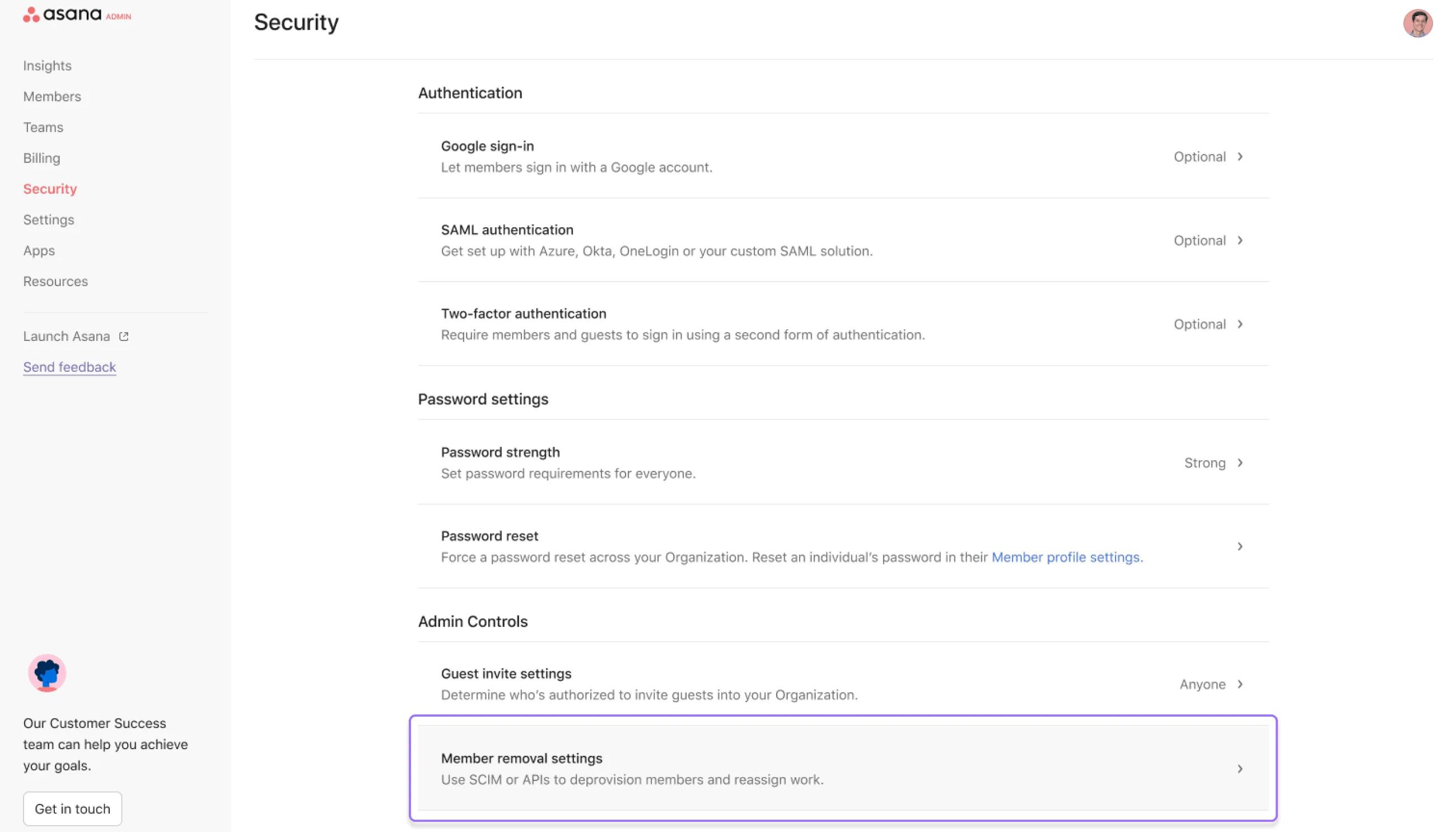
Navigate to Member removal settings in the Security tab of the Admin Console.
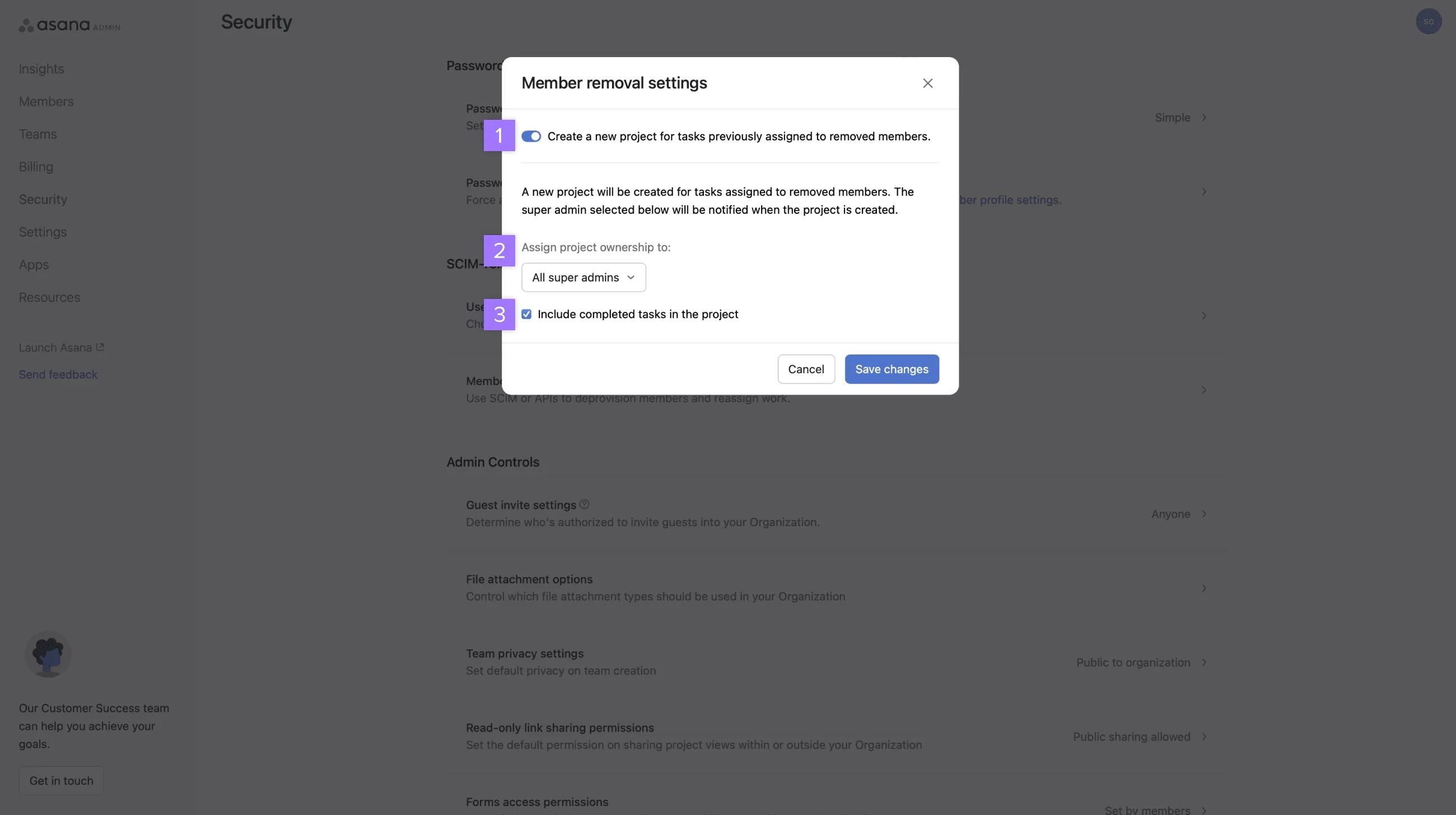
- Toggle on the option Create a new project for tasks previously assigned to removed members.
- Choose All super admins or a specific super admin from the drop-down menu.
- Check the box if you wish to include completed tasks in the project.
Note
These customization settings will only apply when the user is removed from the organization via SCIM or API with a Service Account token.
You will find more information on user deprovisioning in our FAQ article.